
Enterprise Data – Use Case Summary
Enterprises routinely collect and store large volumes of personal and sensitive customer information—names, addresses, birth dates, contact details, and payment credentials. Even with strong network and database protection, breaches remain inevitable, and once attackers extract stored data, traditional encryption alone cannot prevent misuse.
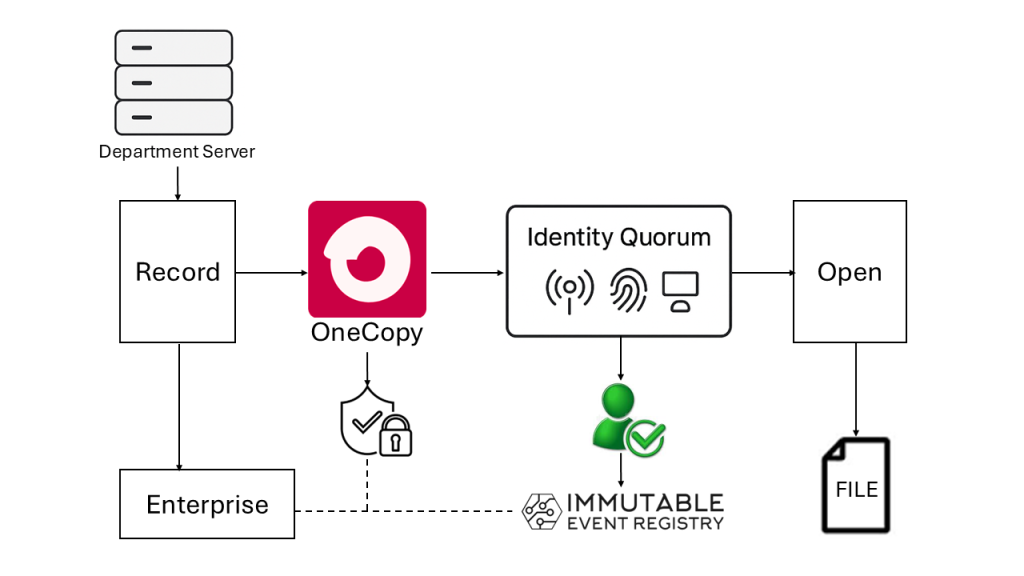
OneCopy changes this model by securing each digital record individually. Every file, record, or export is cryptographically bound to the enterprise’s identity and access policy so that only authorized personnel—verified through OneCopy’s identity quorum—can open or read the content.
Issue
When attackers breach a database, they often gain access to raw, readable files or decrypted data sets during backups or transfers. Current encryption-at-rest solutions protect storage devices, but not the file itself once it leaves the secured system. This gap exposes customer data to leaks, insider threats, and credential misuse.
Enterprises require persistent, file-level protection that continues to enforce access rules even after a breach.Whether you’re a wedding photographer, a commercial videographer, or a content creator, your visuals are among the most valuable assets you own.
The Solution: Applying OneCopy On Enterprise Data At Rest
In this scenario, the enterprise integrates OneCopy-SIFP at the data management layer:
SIFP Enforcement (Kernel Level) – The enterprise installs the SIFP driver on its servers. Every customer record (e.g., customer123.json) is cryptographically signed and sealed with a unique .sifpmeta manifest.
Identity Quorum Configuration – The enterprise admin defines which factors (e.g., hardware TPM key + staff SSO credential + secure environment hash) are required for access.
Access Policy Management – Administrators use the OneCopy Enterprise Console to assign policies by department (e.g., only “Customer Support – Verified Role” can access contact details).
Automated Metadata Sealing – Data pipelines automatically generate .sifpmeta manifests during ingestion or export.
Immutable Audit Trail – All access, modification, and destruction events are logged to the Immutable Event Registry, ensuring compliance with GDPR and data-retention mandates.
Incident Resilience – If attackers exfiltrate the files, they encounter encrypted, self-validating instances bound to the enterprise identity; without valid OneCopy authorization, the files remain unreadable or “not accessible.
Technical Flow Diagram – Enterprise Data At Rest With OneCopy
Outcome
By implementing OneCopy-SIFP, the enterprise ensures that each file enforces its own security policy — independent of databases, passwords, or network defenses. Even in a worst-case breach, customer data remains cryptographically sealed, providing verifiable protection, compliance assurance, and true data sovereignty at rest.
